Providing the best possible solutions and support to our clients is what we do in real life, this time I came with something a client asked for, and I have successfully done it, and since we may need to do it again I said why not I wrote about it.
So, what we have here is the client have Jenkins installed on a virtual machine hosted on azure, also docker and nexus on Linux, the client wants to use Kubernetes for that we have prepared Azure Kubernetes Service (AKS) which offers serverless Kubernetes, an integrated continuous integration and continuous delivery (CI/CD) experience, and enterprise-grade security and governance.
Everything worked well, but now the client wants for some reasons to access the nodes with ssh it may be for maintenance or troubleshooting, for that we are going to see step by step how to connect with SSH to Azure Kubernetes Service.
Configure virtual machine scale set-based AKS clusters for SSH access
To configure your virtual machine scale set-based for SSH access, find the name of your cluster’s virtual machine scale set and add your SSH public key to that scale set.
Use the az aks show command to get the resource group name of your AKS cluster, then the az vmss list command to get the name of your scale set.
As you can see below, inside this resource group I have my AKS :
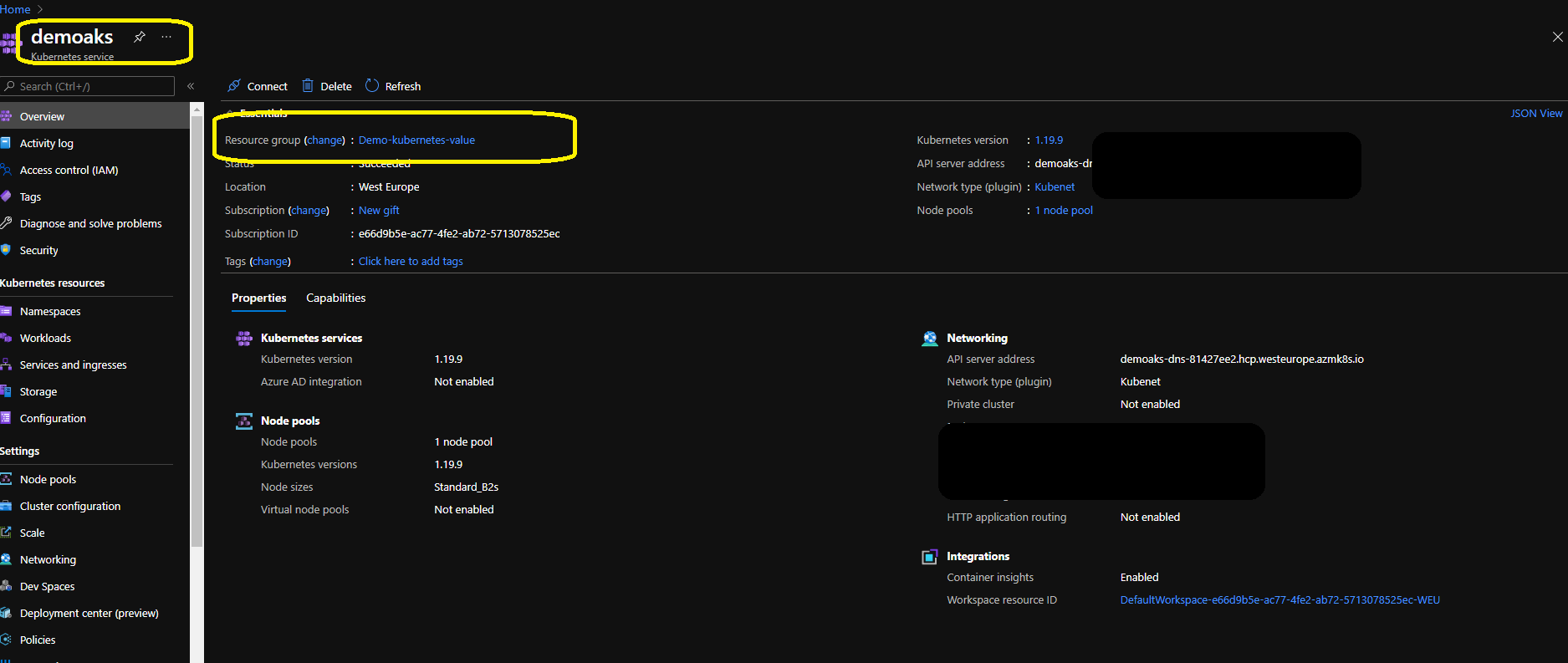 Now you can see our resource group name is “Demo-kubernetes-value” and our Kubernetes service is demoaks.
Now you can see our resource group name is “Demo-kubernetes-value” and our Kubernetes service is demoaks.
First we are going to get our CLUSTER_RESOURCE_GROUP by using the follow command :
az account set --subscription yoursubscription
After that, we are going to take the CLUSTER_RESOURCE_GROUP and the SCALE_SET_NAME using the follow commands :
CLUSTER_RESOURCE_GROUP=$(az aks show --resource-group Demo-kubernetes-value --name demoaks --query nodeResourceGroup -o tsv) SCALE_SET_NAME=$(az vmss list --resource-group $CLUSTER_RESOURCE_GROUP --query '[0].name' -o tsv)
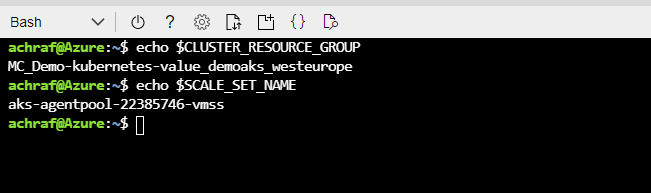
In order to see the values we can use the below commands :
echo $CLUSTER_RESOURCE_GROUP echo $SCALE_SET_NAME
and as you can see below, we will have the following results that we will need them later .
 For Linux nodes as in our case , SSH keys can currently only be added using the Azure CLI.
For Linux nodes as in our case , SSH keys can currently only be added using the Azure CLI.
Add your SSH keys to the nodes
To add your SSH keys to the nodes in a virtual machine scale set, use the az vmss extension set and az vmss update-instances commands.
az vmss extension set \
--resource-group $CLUSTER_RESOURCE_GROUP \
--vmss-name $SCALE_SET_NAME \
--name VMAccessForLinux \
--publisher Microsoft.OSTCExtensions \
--version 1.4 \
--protected-settings "{\"username\":\"azureuser\", \"ssh_key\":\"$(cat ~/.ssh/id_rsa.pub)\"}"
az vmss update-instances --instance-ids '*' \
--resource-group $CLUSTER_RESOURCE_GROUP \
--name $SCALE_SET_NAME
Ps : By default, the username for the AKS nodes is azureuser.
Now we have ssh is activated, for that, and in order to create an SSH connection to an AKS node, you run a helper pod in your AKS cluster. This helper pod provides you with SSH access into the cluster and then additional SSH node access
1 – We need to run container image and attach a terminal session to it. This container can be used to create an SSH session with any node in the AKS cluster :
kubectl run -it --rm aks-ssh --image=mcr.microsoft.com/aks/fundamental/base-ubuntu:v0.0.11 or kubectl run -it --rm aks-ssh --image=debian
2- Now we need to install SSH client :
apt-get update && apt-get install openssh-client -y
3-Open a new terminal window, not connected to your container, copy your private SSH key into the helper pod. This private key is used to create the SSH into the AKS node.
kubectl cp ~/.ssh/id_rsa $(kubectl get pod -l run=aks-ssh -o jsonpath='{.items[0].metadata.name}'):/id_rsa
4-Return to the terminal session to your container, update the permissions on the copied id_rsa private SSH key so that it is user read-only ;
chmod 0400 id_rsa
5- Now the last step is to connect to your AKS node :
#the first command will give us the nodes with their IP addresses kubectl get nodes -o wide #this command will set up a connection between the node IP that you have chosen using the ssh id_rsa ssh -i id_rsa azureuser@ip
When done, exit the SSH session and then exit the interactive container session. When this container session closes, the pod used for SSH access from the AKS cluster is deleted .
















This is far better than official Azure documentation thank you
Thank you so much , this mean a lot to me .